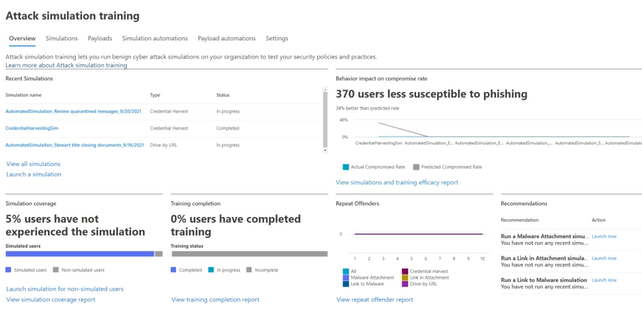
We offer Phishing Simulations
CyberProtex customizes phishing simulation attacks using Social engineering techniques
|
We work with companies to customize phishing simulation attacks. Customers select an available social engineering technique, which was curated from the MITRE ATT&CK® framework, our software prepares different payloads available for different techniques.
https://attack.mitre.org/techniques/enterprise/ |
Payloads Creation using WYSIWYG
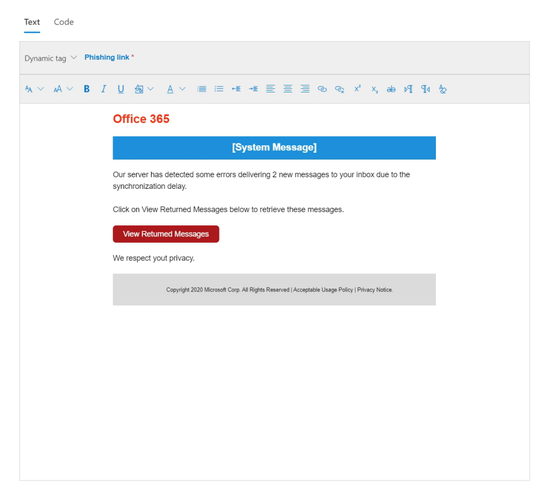
A payload is the phishing email message and links or attachment content that's are presented to users in simulations. CyberProtex's Attack simulations offers a robust built-in payload catalog for the available social engineering techniques. We work with customers to create custom payloads that will work better for your organization.
The following details are shown for each payload:
Payload name
Language: The language of the payload content. Microsoft's payload catalog (global) provides payloads in 10+ languages which can also be filtered.
Click rate: How many people have clicked on this payload.
Predicted compromise rate: Historical data for the payload across Microsoft 365 that predicts the percentage of people who will get compromised by this payload.
The following details are shown for each payload:
Payload name
Language: The language of the payload content. Microsoft's payload catalog (global) provides payloads in 10+ languages which can also be filtered.
Click rate: How many people have clicked on this payload.
Predicted compromise rate: Historical data for the payload across Microsoft 365 that predicts the percentage of people who will get compromised by this payload.
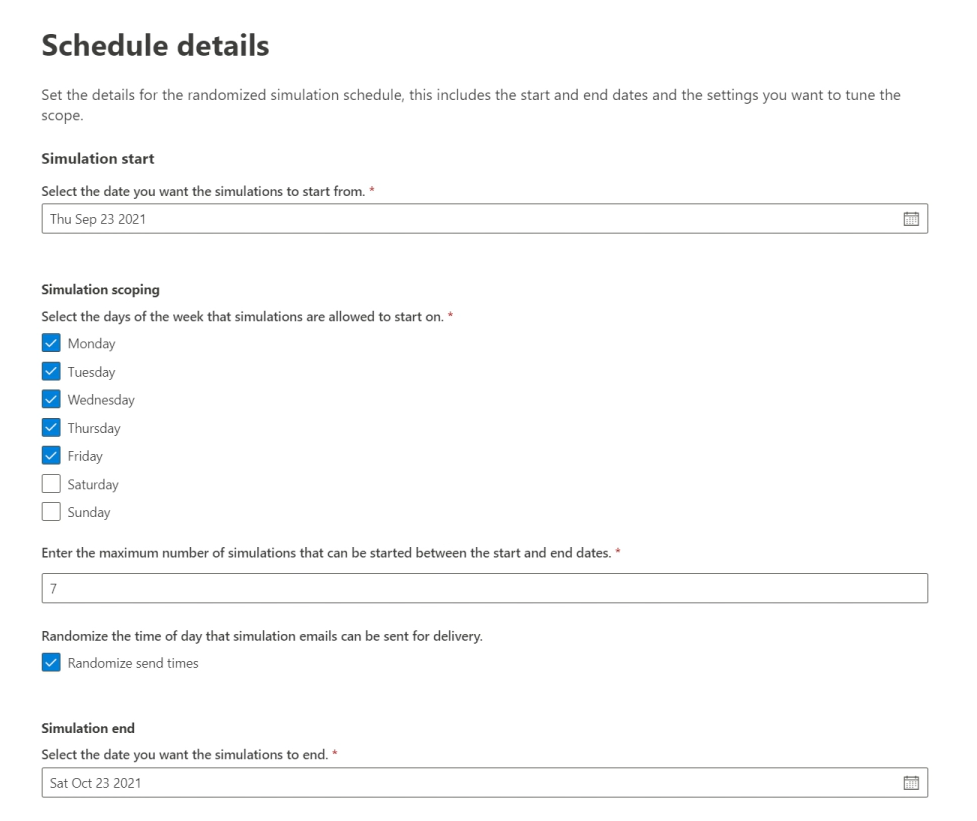
Scheduler - Attack Simulator
|
We offer the following social engineering techniques using our custom scheduler:
Credential harvest: Attempts to collect credentials by taking users to a well-known looking website with input boxes to submit a username and password. Malware attachment: Adds a malicious attachment to a message. When the user opens the attachment, arbitrary code is run that will help the attacker compromise the target's device. Link in attachment: A type of credential harvest hybrid. An attacker inserts a URL into an email attachment. The URL within the attachment follows the same technique as credential harvest. Link to malware: Runs some arbitrary code from a file hosted on a well-known file sharing service. The message sent to the user will contain a link to this malicious file. Opening the file will help the attacker compromise the target's device. Drive-by URL: The malicious URL in the message takes the user to a familiar-looking website that silently runs and/or installs code on the user's device. |
Contact Us Today |
For more information about Cyber Security from trusted sources check out: For more information about cyber-bullying for teens and parents check out:
|