Protecting Critical Infrastructure
Industrial Control Systems (ICS) and SCADA Essentials
Training and Simulation
The U.S. Critical Infrastructure, including water treatment pumps, gas pipelines, Nuclear Power Plants, and Electrical grid’s distribution systems—which carry electricity from transmission systems to consumers and are regulated primarily by states—are increasingly at risk from cyberattacks. Distribution systems are growing more vulnerable, in part because their industrial control systems increasingly allow remote access and connect to business networks. As a result, threat actors can use multiple techniques to access those systems and potentially disrupt operations. However, the scale of potential impacts from such attacks is not well understood.
Distribution utilities included in GAO’s review are generally not subject to mandatory federal cybersecurity standards, but they, and selected states, had taken actions intended to improve distribution systems’ cybersecurity. These actions included incorporating cybersecurity into routine oversight processes and hiring dedicated cybersecurity personnel. Federal agencies have supported these actions by, for example, providing cybersecurity training and guidance.
Distribution utilities included in GAO’s review are generally not subject to mandatory federal cybersecurity standards, but they, and selected states, had taken actions intended to improve distribution systems’ cybersecurity. These actions included incorporating cybersecurity into routine oversight processes and hiring dedicated cybersecurity personnel. Federal agencies have supported these actions by, for example, providing cybersecurity training and guidance.
This course provides students with the essentials for conducting cybersecurity work in industrial control systems (ICS) and SCADA environments.
Various threat actors are increasingly capable of carrying out a cyberattack on the grid’s distribution systems, according to all of the national laboratory officials we interviewed. Nations, criminal groups, terrorists, hackers and hacktivists, and insiders pose threats to the bulk power system.
This course covers a broad overview of the following:
This course covers a broad overview of the following:
- Threats, Attacks and Vulnerabilities course provides an overview of ICS
- How to create Simulation Environments in Docker
- How to control system attacks, methods, and tools
- Approaches to system and network defense architectures and techniques
- Incident response skills in a control system environment
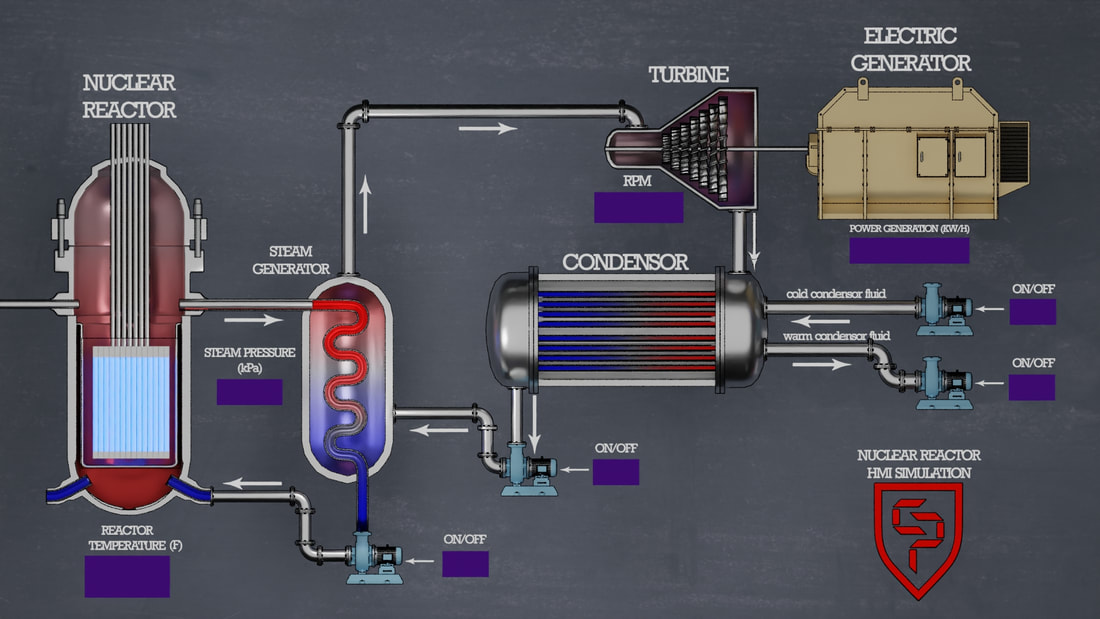
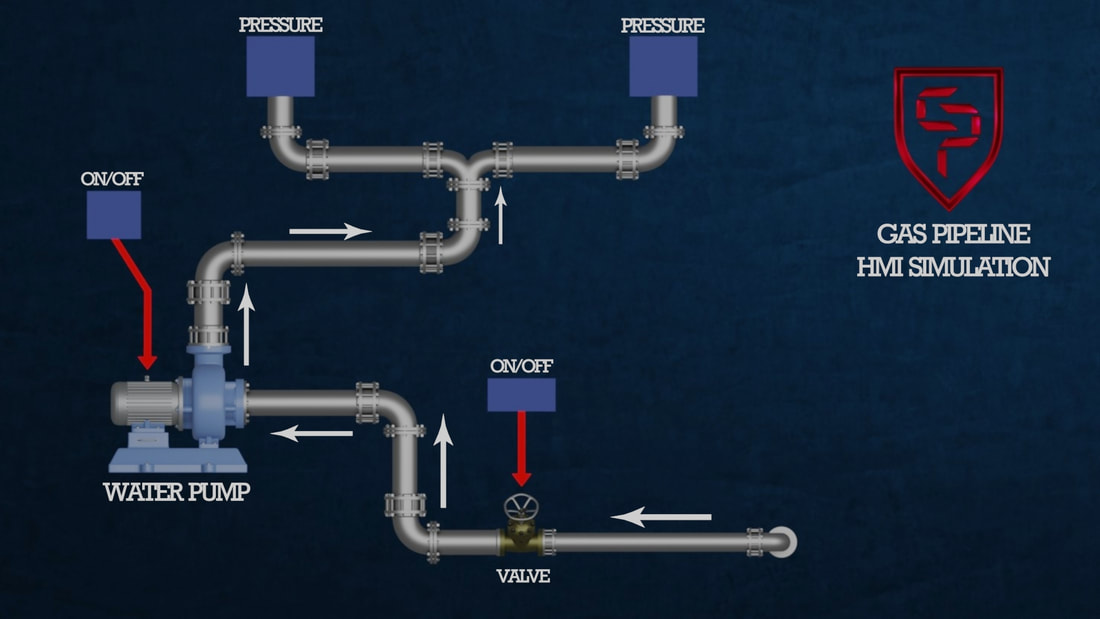
CyberProtex - ICS / SCADA Simulations
We customize each of the following environments and deliver hands-on training via Azure Labs. Each Simulation is created for specific training to teach students about Nuclear Reactors, Water Tanks, Dams, Electrical Grids and Gas Pipelines