Have you been hit by Ransomware?
We can help!
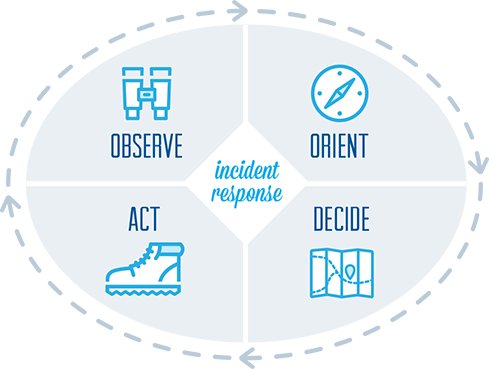
Incident response (IR) is the systematic approach taken by an organization to prepare for, detect, contain, and recover from a suspected cybersecurity breach. CyberProtex assists our customers in building incident response plans that helps ensure an orderly and effective response to cybersecurity incidents, which in turn can help protect an organization’s data, reputation, and revenue.
Common Incidents Addressed by our Cyber Response Team
Ransomware
Insider Threat and Accidental Data Loss
Phishing
Malware, Keyloggers, & Backdoors
Denial-of-Service (DoS)
Web application
Advance Persistent Threats (APT)
Ransomware
Insider Threat and Accidental Data Loss
Phishing
Malware, Keyloggers, & Backdoors
Denial-of-Service (DoS)
Web application
Advance Persistent Threats (APT)