CyberLMS
Learning Management Software
CyberProtex’s proprietary “Cyber Learning Management System” or CyberLMS is a software platform we developed to deliver live online instruction and pre-recorded on-demand instruction, as well as access to interactive virtual study tools and games that are designed to reach and engage students and adults of all learning styles.
Contact us today for a FREE TRIAL!
Contact us today for a FREE TRIAL!
CyberLMS Software
Track Progress
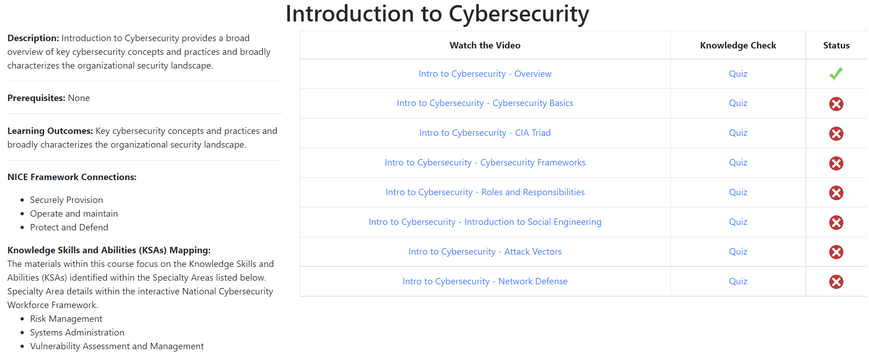
Our software tracks the progress of each user and provide a certificate of completion for each student.
Screenshot Example Provided below:
Screenshot Example Provided below:
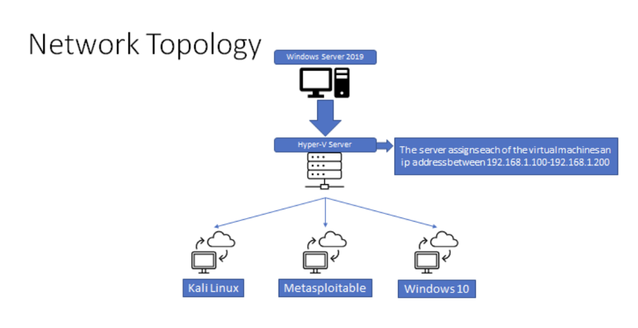
Hands-On Labs
Lab Services - Cyber Range
Animated Videos
CyberProtex is very experienced with creating dynamic training videos/modules on a wide variety of topics, and can create custom modules that are interesting and engaging and that educators can access from home or in a group setting.
CYBERLMS - AVAILABLE CERTIFICATION PREPARATION COURSES
CompTIA Security+CompTIA(c) Security+ Certification covers the essentials in understanding best practices in Network Security and Risk Management. This comprehensive course will prepare the participant to take the Security + exam. Topics include: Network Security, Compliance, Threats, Vulnerabilities, Malware, Penetration Testing, Application, Data & Host Security, Access Control & Identity Management, and Cryptography. Security+ five-day bootcamp is available on demand for groups of 8 or more. Security+ five-day online boot camp is available to individuals on our regularly scheduled calendar. See website.
CompTIA Cybersecurity Analyst+The Analyst+ is a mid-level course for professionals that has already passed the Security+. The behavioral analytics skills covered by CSA+ identify and combat malware and advanced persistent threats (APTs), resulting in enhanced threat visibility across a broad attack surface. CompTIA CSA+ is for IT professionals looking to gain the following security analyst skills: Configure and use threat detection tools; Perform data analysis; and Interpret the results to identify vulnerabilities, threats and risks to an organization. This 5-day boot camp course is available on demand for groups of 8 or more.
CompTIA Advanced Security Practitioner (CASP)The goal in this advanced course is to prepare students to take and pass the CompTIA Advanced Security Practitioner (CASP) exam, as well as to help students gain a solid understanding of the concepts addressed in this topic so they can apply them to their work in the field. CompTIA Advanced Security Practitioner (CASP) meets the growing demand for advanced IT security in the enterprise. Recommended for IT professionals with at least 5 years of experience, CASP certifies critical thinking and judgment across a broad spectrum of security disciplines and requires candidates to implement clear solutions in complex environments. This 5-day boot camp course is available on demand for groups of 8 or more.
EC|Council Certification CEH: Certified Ethical HackerThis advanced training course for the EC Council Certified Ethical Hacker exam will provide professionals the knowledge and skills that hackers use to target systems so that professionals can work legally and ethically to improve security systems. Participants will be prepared to take the EC|Council CEH exam. Topics include: Malware Operations, Mobile Technologies, Risk Assessments, Firewalls, Cryptography, Threat Modeling, Vulnerabilities, Testing and Professional Standards. Certified Ethical Hacker five-day bootcamp is available on demand for groups of 6 or more. CEH five-day boot camp is available to individuals on our regularly scheduled calendar. See website.
EC|Council CND: Certified Network DefenderThis advanced course is designed to provide Network Administrators the skills and knowledge to protect, detect and mitigate network attacks. The goal of this course is to prepare the participant to take the EC|Council CND exam. Topics include: Network Security Threats, Vulnerabilities & Attacks; Controls, Protocols & Devices; Policy Design & Implementation; Physical Security; Wireless Network Defense; Network Traffic Monitoring & Analysis; Network Risk & Vulnerability Management; and Data Backup & Recovery. Certified Network Defender five-day bootcamp is available on demand for groups of 6 or more. CND five-day boot camp is available to individuals on our regularly scheduled calendar. See website.
EC| Council ESCA: EC-COUNCIL CERTIFIED SECURITY ANALYSTThe ECSA penetration testing program takes the tools and techniques you learned in the Certified Ethical Hacker course (CEH) and elevates your ability by teaching you how to apply the skills learned in the CEH. This ECSA penetration testing course provides you with a real world hands-on penetration testing experience and is a globally accepted hacking and penetration testing class available that covers the testing of modern infrastructures, operating systems and application environments while teaching the students how to document and write a penetration testing report. This 5-day boot camp course is available on demand for groups of 5 or more.
ISC2 Certified Authorization Professional (CAP)The goal in this course is to prepare professionals to take the CAP - Certified Authorization Professional exam, and to help them gain a solid understanding of the concepts addressed in topic so that they can apply them to their work in the field. The CAP certification is an objective measure of the knowledge, skills and abilities required for personnel involved in the process of authorizing and maintaining information systems. The CAP examination tests the breadth and depth of a candidate’s knowledge by focusing on the 7 domains of the CAP CBK: Risk Management Framework (RMF), Categorization of Information Systems, Selection of Security Controls, Security Control Implementation, Security Control Assessment, Information System Authorization, and Monitoring of Security Controls. This 5-day boot camp course is available on demand for groups of 8 or more.
ISC2 Certified Information System Security Practitioner – (CISSP)The vendor-neutral CISSP certification is the ideal credential for those with proven deep technical and managerial competence, skills, experience, and credibility to design, engineer, implement, and manage their overall information security program to protect organizations from growing sophisticated attacks. One of our most popular courses year after year, this advanced course will prepare the Information Systems professional to take the (ISC)² CISSP exam. Topics include: Security and Risk Management, Asset Security, Engineering for secure systems and software, Secure Networks; Identity & Access Management, Security Assessment & Testing, and Security Operations. The CISSP five-day bootcamp is available on demand for groups of 8 or more. CISSP five-day boot camp is available to individuals on our regularly scheduled calendar. See website.
ISC2 Certified Information System Security Practitioner – CISSP CONCENTRATIONSCISSP-ISSAP: Information Systems Security Architecture ProfessionalThe CISSP-ISSAP is an advanced concentration for Chief Security Architects and Analysts who hold the CISSP certification and have worked for two years in IS Security Architecture. The architect plays a key role within the information security department with responsibilities for developing, designing, or analyzing the overall security plan. This course will prepare the professional in the topics on the CISSP-ISSAP certification exam. The CISSP-ISSAP 5-day boot camp course is available on demand for groups of 5 or more.
CISSP-ISSEP: Information Systems Security Engineering ProfessionalThe CISSP-ISSEP credential was developed in conjunction with the U.S. National Security Agency (NSA) providing an invaluable tool for any systems security engineering professional. For the professional who already holds the CISSP certification, the ISSEP is the guide for incorporating security into projects, applications, business processes, and all information systems. This course will prepare the professional in the topics on the CISSP-ISSEP certification exam. The CISSP-ISSEP 5-day boot camp course is available on demand for groups of 5 or more.
CISSP-ISSMP: Information Systems Security Management ProfessionalThe CISSP-ISSMP credential contains deep managerial elements, including project management, risk management, setting up and delivering a security awareness program, and managing a business continuity planning program. This certification is for professionals who hold the CISSP and are ready to go further to establish, present, and govern information security programs. This course will prepare the professional in the topics on the CISSP-ISSMP certification exam. The CISSP-ISSMP 5-day boot camp course is available on demand for groups of 5 or more.
ISACA CISA Certified Information Systems AuditorThis course prepares the participant in the topics on the Certified Information Systems Auditor exam. Professionals with the CISA certification are recognized among the most-qualified and sought-after IS audit, control and security professionals. ISACA's globally accepted CISA certification showcases your experience, knowledge and abilities. The CISA 5-day boot camp course is available on demand for groups of 8 or more.
ISACA CISM Certified Information Security ManagerThis course prepares the participant to take and pass the Certified Information Security Manager exam. Earning the CISM can secure your place among the most in-demand information security management professionals with the ability to configure information security programs to advance broader enterprise goals and objectives. The CISM 3-day boot camp course is available on our regularly scheduled calendar. See website.
Python Programming for Cyber SecurityThe CyberProtex "Python for Cyber" Course follows the Department of Homeland Security (DHS) Workforce Framework. The Framework is the foundation for increasing the size and capability of the US cybersecurity workforce. CyberProtex has partnered with the Department of Homeland Security to implement the Workforce Framework through the National Initiative for Cybersecurity Education (NICE). Python is a widely used general-purpose, high-level programming language. Its design philosophy emphasizes code readability, and its syntax allows programmers to express concepts in fewer lines of code than would be possible in languages such as C++, or Java. Cyber Security works best when implemented at the earliest point possible. This course teaches the participant how to work Cyber Security considerations into their Python programming. This three-day Python Programming for Cyber Security course is available on demand for groups of 8 or more.
Risk Management Framework - NIST 800-53The CyberProtex "Risk Management Framework (RMF)" Course follows the Department of Homeland Security (DHS) Workforce Framework. The Workforce Framework is the foundation for increasing the size and capability of the US cybersecurity workforce. CyberProtex has partnered with the Department of Homeland Security to implement the Workforce Framework through the National Initiative for Cybersecurity Education (NICE). Topics for this course include: Introduction to the RMF, Managing Risk at the Enterprise, and Threats and Vulnerabilities. This course will break down for the professional the steps of the RMF: Categorizing the System; Selecting Baseline Controls; Risk Assessments and Refining; System Security Planning, Implementation of controls; Assessing the Controls, Determining and Accepting the Risk; Seeking the Authority to Operate; and Continuous Monitoring of the System. There will be Labs and practical exercises to strengthen the participants learning, using our CyberNinja Test Prep Software and our Simulated eMASS Engine (SEE). This three-day Risk Management Framework course is available on demand for groups of 8 or more.
Security and Risk ManagementThis beginning level course covers Security and Risk Management concepts to ensure compliance and business continuity. This course covers: Confidentiality, integrity and availability concepts; Security governance principles; Compliance; Regulatory & legal issues; Professional ethics; and Security standards, policies, procedures and guidelines. This three-day Security and Risk Management course is available on demand for groups of 8 or more.
Threats and Vulnerabilities for ManagersThis very popular introductory course is a great place to start in understanding the basics of Threats, Vulnerabilities and Attacks. This course is designed to provide management and other professionals an understanding of the vulnerabilities in information systems, to better prepare them to mitigate attacks. Topics include: Network security Concerns; Network Reconnaissance Attacks; Network Access Attacks; DoS and DDoS; Malware Attacks and Viruses. This three-day Threats and Vulnerabilities for Managers course is available on demand for groups of 8 or more.
CompTIA Security+CompTIA(c) Security+ Certification covers the essentials in understanding best practices in Network Security and Risk Management. This comprehensive course will prepare the participant to take the Security + exam. Topics include: Network Security, Compliance, Threats, Vulnerabilities, Malware, Penetration Testing, Application, Data & Host Security, Access Control & Identity Management, and Cryptography. Security+ five-day bootcamp is available on demand for groups of 8 or more. Security+ five-day online boot camp is available to individuals on our regularly scheduled calendar. See website.
CompTIA Cybersecurity Analyst+The Analyst+ is a mid-level course for professionals that has already passed the Security+. The behavioral analytics skills covered by CSA+ identify and combat malware and advanced persistent threats (APTs), resulting in enhanced threat visibility across a broad attack surface. CompTIA CSA+ is for IT professionals looking to gain the following security analyst skills: Configure and use threat detection tools; Perform data analysis; and Interpret the results to identify vulnerabilities, threats and risks to an organization. This 5-day boot camp course is available on demand for groups of 8 or more.
CompTIA Advanced Security Practitioner (CASP)The goal in this advanced course is to prepare students to take and pass the CompTIA Advanced Security Practitioner (CASP) exam, as well as to help students gain a solid understanding of the concepts addressed in this topic so they can apply them to their work in the field. CompTIA Advanced Security Practitioner (CASP) meets the growing demand for advanced IT security in the enterprise. Recommended for IT professionals with at least 5 years of experience, CASP certifies critical thinking and judgment across a broad spectrum of security disciplines and requires candidates to implement clear solutions in complex environments. This 5-day boot camp course is available on demand for groups of 8 or more.
EC|Council Certification CEH: Certified Ethical HackerThis advanced training course for the EC Council Certified Ethical Hacker exam will provide professionals the knowledge and skills that hackers use to target systems so that professionals can work legally and ethically to improve security systems. Participants will be prepared to take the EC|Council CEH exam. Topics include: Malware Operations, Mobile Technologies, Risk Assessments, Firewalls, Cryptography, Threat Modeling, Vulnerabilities, Testing and Professional Standards. Certified Ethical Hacker five-day bootcamp is available on demand for groups of 6 or more. CEH five-day boot camp is available to individuals on our regularly scheduled calendar. See website.
EC|Council CND: Certified Network DefenderThis advanced course is designed to provide Network Administrators the skills and knowledge to protect, detect and mitigate network attacks. The goal of this course is to prepare the participant to take the EC|Council CND exam. Topics include: Network Security Threats, Vulnerabilities & Attacks; Controls, Protocols & Devices; Policy Design & Implementation; Physical Security; Wireless Network Defense; Network Traffic Monitoring & Analysis; Network Risk & Vulnerability Management; and Data Backup & Recovery. Certified Network Defender five-day bootcamp is available on demand for groups of 6 or more. CND five-day boot camp is available to individuals on our regularly scheduled calendar. See website.
EC| Council ESCA: EC-COUNCIL CERTIFIED SECURITY ANALYSTThe ECSA penetration testing program takes the tools and techniques you learned in the Certified Ethical Hacker course (CEH) and elevates your ability by teaching you how to apply the skills learned in the CEH. This ECSA penetration testing course provides you with a real world hands-on penetration testing experience and is a globally accepted hacking and penetration testing class available that covers the testing of modern infrastructures, operating systems and application environments while teaching the students how to document and write a penetration testing report. This 5-day boot camp course is available on demand for groups of 5 or more.
ISC2 Certified Authorization Professional (CAP)The goal in this course is to prepare professionals to take the CAP - Certified Authorization Professional exam, and to help them gain a solid understanding of the concepts addressed in topic so that they can apply them to their work in the field. The CAP certification is an objective measure of the knowledge, skills and abilities required for personnel involved in the process of authorizing and maintaining information systems. The CAP examination tests the breadth and depth of a candidate’s knowledge by focusing on the 7 domains of the CAP CBK: Risk Management Framework (RMF), Categorization of Information Systems, Selection of Security Controls, Security Control Implementation, Security Control Assessment, Information System Authorization, and Monitoring of Security Controls. This 5-day boot camp course is available on demand for groups of 8 or more.
ISC2 Certified Information System Security Practitioner – (CISSP)The vendor-neutral CISSP certification is the ideal credential for those with proven deep technical and managerial competence, skills, experience, and credibility to design, engineer, implement, and manage their overall information security program to protect organizations from growing sophisticated attacks. One of our most popular courses year after year, this advanced course will prepare the Information Systems professional to take the (ISC)² CISSP exam. Topics include: Security and Risk Management, Asset Security, Engineering for secure systems and software, Secure Networks; Identity & Access Management, Security Assessment & Testing, and Security Operations. The CISSP five-day bootcamp is available on demand for groups of 8 or more. CISSP five-day boot camp is available to individuals on our regularly scheduled calendar. See website.
ISC2 Certified Information System Security Practitioner – CISSP CONCENTRATIONSCISSP-ISSAP: Information Systems Security Architecture ProfessionalThe CISSP-ISSAP is an advanced concentration for Chief Security Architects and Analysts who hold the CISSP certification and have worked for two years in IS Security Architecture. The architect plays a key role within the information security department with responsibilities for developing, designing, or analyzing the overall security plan. This course will prepare the professional in the topics on the CISSP-ISSAP certification exam. The CISSP-ISSAP 5-day boot camp course is available on demand for groups of 5 or more.
CISSP-ISSEP: Information Systems Security Engineering ProfessionalThe CISSP-ISSEP credential was developed in conjunction with the U.S. National Security Agency (NSA) providing an invaluable tool for any systems security engineering professional. For the professional who already holds the CISSP certification, the ISSEP is the guide for incorporating security into projects, applications, business processes, and all information systems. This course will prepare the professional in the topics on the CISSP-ISSEP certification exam. The CISSP-ISSEP 5-day boot camp course is available on demand for groups of 5 or more.
CISSP-ISSMP: Information Systems Security Management ProfessionalThe CISSP-ISSMP credential contains deep managerial elements, including project management, risk management, setting up and delivering a security awareness program, and managing a business continuity planning program. This certification is for professionals who hold the CISSP and are ready to go further to establish, present, and govern information security programs. This course will prepare the professional in the topics on the CISSP-ISSMP certification exam. The CISSP-ISSMP 5-day boot camp course is available on demand for groups of 5 or more.
ISACA CISA Certified Information Systems AuditorThis course prepares the participant in the topics on the Certified Information Systems Auditor exam. Professionals with the CISA certification are recognized among the most-qualified and sought-after IS audit, control and security professionals. ISACA's globally accepted CISA certification showcases your experience, knowledge and abilities. The CISA 5-day boot camp course is available on demand for groups of 8 or more.
ISACA CISM Certified Information Security ManagerThis course prepares the participant to take and pass the Certified Information Security Manager exam. Earning the CISM can secure your place among the most in-demand information security management professionals with the ability to configure information security programs to advance broader enterprise goals and objectives. The CISM 3-day boot camp course is available on our regularly scheduled calendar. See website.
Python Programming for Cyber SecurityThe CyberProtex "Python for Cyber" Course follows the Department of Homeland Security (DHS) Workforce Framework. The Framework is the foundation for increasing the size and capability of the US cybersecurity workforce. CyberProtex has partnered with the Department of Homeland Security to implement the Workforce Framework through the National Initiative for Cybersecurity Education (NICE). Python is a widely used general-purpose, high-level programming language. Its design philosophy emphasizes code readability, and its syntax allows programmers to express concepts in fewer lines of code than would be possible in languages such as C++, or Java. Cyber Security works best when implemented at the earliest point possible. This course teaches the participant how to work Cyber Security considerations into their Python programming. This three-day Python Programming for Cyber Security course is available on demand for groups of 8 or more.
Risk Management Framework - NIST 800-53The CyberProtex "Risk Management Framework (RMF)" Course follows the Department of Homeland Security (DHS) Workforce Framework. The Workforce Framework is the foundation for increasing the size and capability of the US cybersecurity workforce. CyberProtex has partnered with the Department of Homeland Security to implement the Workforce Framework through the National Initiative for Cybersecurity Education (NICE). Topics for this course include: Introduction to the RMF, Managing Risk at the Enterprise, and Threats and Vulnerabilities. This course will break down for the professional the steps of the RMF: Categorizing the System; Selecting Baseline Controls; Risk Assessments and Refining; System Security Planning, Implementation of controls; Assessing the Controls, Determining and Accepting the Risk; Seeking the Authority to Operate; and Continuous Monitoring of the System. There will be Labs and practical exercises to strengthen the participants learning, using our CyberNinja Test Prep Software and our Simulated eMASS Engine (SEE). This three-day Risk Management Framework course is available on demand for groups of 8 or more.
Security and Risk ManagementThis beginning level course covers Security and Risk Management concepts to ensure compliance and business continuity. This course covers: Confidentiality, integrity and availability concepts; Security governance principles; Compliance; Regulatory & legal issues; Professional ethics; and Security standards, policies, procedures and guidelines. This three-day Security and Risk Management course is available on demand for groups of 8 or more.
Threats and Vulnerabilities for ManagersThis very popular introductory course is a great place to start in understanding the basics of Threats, Vulnerabilities and Attacks. This course is designed to provide management and other professionals an understanding of the vulnerabilities in information systems, to better prepare them to mitigate attacks. Topics include: Network security Concerns; Network Reconnaissance Attacks; Network Access Attacks; DoS and DDoS; Malware Attacks and Viruses. This three-day Threats and Vulnerabilities for Managers course is available on demand for groups of 8 or more.