Improve your regulatory compliance
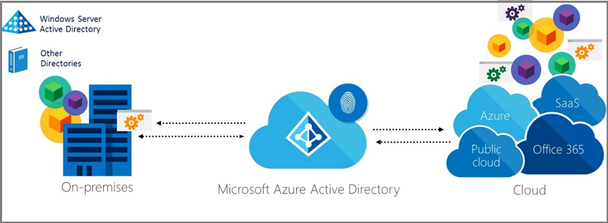
Microsoft’s identity solutions span on-premises and cloud-based capabilities,
creating a single user identity for authentication and authorization to all resources, regardless of location.
Microsoft’s identity solutions span on-premises and cloud-based capabilities,
creating a single user identity for authentication and authorization to all resources, regardless of location.
Modernize your IT |
Cut IT operational cost |
Secure cloud assets |
Evaluate your regulatory compliance using the Regulatory compliance dashboards
Improve your compliance posture by taking action on recommendations
Are you ready for Microsoft 365?
Is your company looking to cut IT operational cost?
Is your company looking to secure cloud assets (SaaS apps, infrastructure)?
Is your company looking to modernize your IT?
CyberProtex provides technical expertise and thought leadership to help your growing enterprise most effectively achieve its current and future IT objectives by helping you efficiently utilize your existing resources and recommending upgrades that best suit your needs.
Our expert Enterprise Architecture services include analyzing customers' existing network infrastructure and making sound recommendations for architectural implementations that will improve performance; identifying vulnerabilities and making recommendations for practical tools and products to improve customers' IT security posture; and helping customers be better stewards of their existing IT resources.
Is your company looking to secure cloud assets (SaaS apps, infrastructure)?
Is your company looking to modernize your IT?
CyberProtex provides technical expertise and thought leadership to help your growing enterprise most effectively achieve its current and future IT objectives by helping you efficiently utilize your existing resources and recommending upgrades that best suit your needs.
Our expert Enterprise Architecture services include analyzing customers' existing network infrastructure and making sound recommendations for architectural implementations that will improve performance; identifying vulnerabilities and making recommendations for practical tools and products to improve customers' IT security posture; and helping customers be better stewards of their existing IT resources.
How can YOU benefit from Microsoft 365?

Whether you are a small business that has grown out of its network and is ready to upgrade its enterprise management system or you are a large business having troubleshooting issues with your network design or enterprise management, CyberProtex can help securely link your existing IT infrastructure to your vision for the future.
CyberProtex's experience with many of the leading enterprise level software (i.e. SAP, Microsoft, Dynamics, Oracle,) lets us assist your team in refining its processes, helping with its IT strategy, and assessing the current and future needs of your company or organization. Contact Us today to schedule a consultation. |