Certified Network Defender (CND)
Protect, Detect and Respond
EC Council CND
|
Information HereEmail [email protected] |
Course Description
The EC-Council Certified Network Defender (CND) is a vendor-neutral, hands-on, instructor-led comprehensive network security certification training program. It is a skills-based, lab intensive program based on a job-task analysis and cyber security education framework presented by the National Initiative of Cybersecurity Education (NICE). The course has also been mapped to global job roles and responsibilities and the Department of Defense (DoD) job roles for system/network administrators.
The course is designed and developed after extensive market research and surveys. The program prepares network administrators on network security technologies and operations to attain Defense - in - Depth network security preparedness. It covers the protect, detect and respond approach to network security.
The course contains hands-on labs, based on major network security tools and techniques which will provide network administrators real world expertise on current network security technologies and operations. The study-kit provides you with over 10 GB of network security best practices, assessments and protection tools. The kit also contains templates for various network policies and a large number of white papers for additional learning. The exam will be given at the CyberProtex training center in Madison.
Course Duration: 5 days
Group discounts are available. Course price is $2695 per person and includes study book and voucher.
Contact Us for more information.
The EC-Council Certified Network Defender (CND) is a vendor-neutral, hands-on, instructor-led comprehensive network security certification training program. It is a skills-based, lab intensive program based on a job-task analysis and cyber security education framework presented by the National Initiative of Cybersecurity Education (NICE). The course has also been mapped to global job roles and responsibilities and the Department of Defense (DoD) job roles for system/network administrators.
The course is designed and developed after extensive market research and surveys. The program prepares network administrators on network security technologies and operations to attain Defense - in - Depth network security preparedness. It covers the protect, detect and respond approach to network security.
The course contains hands-on labs, based on major network security tools and techniques which will provide network administrators real world expertise on current network security technologies and operations. The study-kit provides you with over 10 GB of network security best practices, assessments and protection tools. The kit also contains templates for various network policies and a large number of white papers for additional learning. The exam will be given at the CyberProtex training center in Madison.
Course Duration: 5 days
Group discounts are available. Course price is $2695 per person and includes study book and voucher.
Contact Us for more information.
This comprehensive course is designed to provide Network Administrators the skills and knowledge to protect, detect and mitigate network attacks. The participant of this course will be ready to take the EC|Council CND exam.
Outline of topics:
Outline of topics:
|
Module 01: Computer Network and Defense Fundamentals
|
Module 06: Host Security
Module 12: Network Risk and Vulnerability Management Module 13: Data Backup and Recovery Module 14: Network Incident Response and Management |
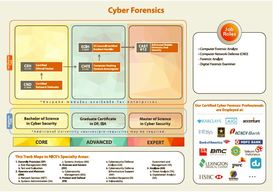
To download and read the complete EC Council Cyber Program Guide (pdf) click on photo to right or click here. |
PLEASE NOTE: In some cases, vouchers for exams may only be obtained by the individual taking the exam. In those cases, we reserve the right to refund the cost of the voucher to the person taking the course from us with the intent they will take the refund and pay for the voucher themselves.
All courses are subject to cancellation and/or rescheduling due to insufficient enrollment or unforeseen circumstances, as per CyberProtex Policy. Additionally, if for some unforeseen reason an instructor cannot be available at any particular time, we will notify the attendees of the class as soon as possible and allow a makeup time for the missed instruction due to the instructors' absence.
All courses are subject to cancellation and/or rescheduling due to insufficient enrollment or unforeseen circumstances, as per CyberProtex Policy. Additionally, if for some unforeseen reason an instructor cannot be available at any particular time, we will notify the attendees of the class as soon as possible and allow a makeup time for the missed instruction due to the instructors' absence.